Chip 8 - HackTM Quals 2020
CHIP 8 /1
The challenge was as follows:
I made this sweet web-based chip8 emulator.
The first 512 bytes of memory are protected!
http://167.172.165.153:60003/
Note: This challenge can be solved using only chip8 instructions.
We were given a chip8 emulator with a basic interface as follows:

And the following list of commands:

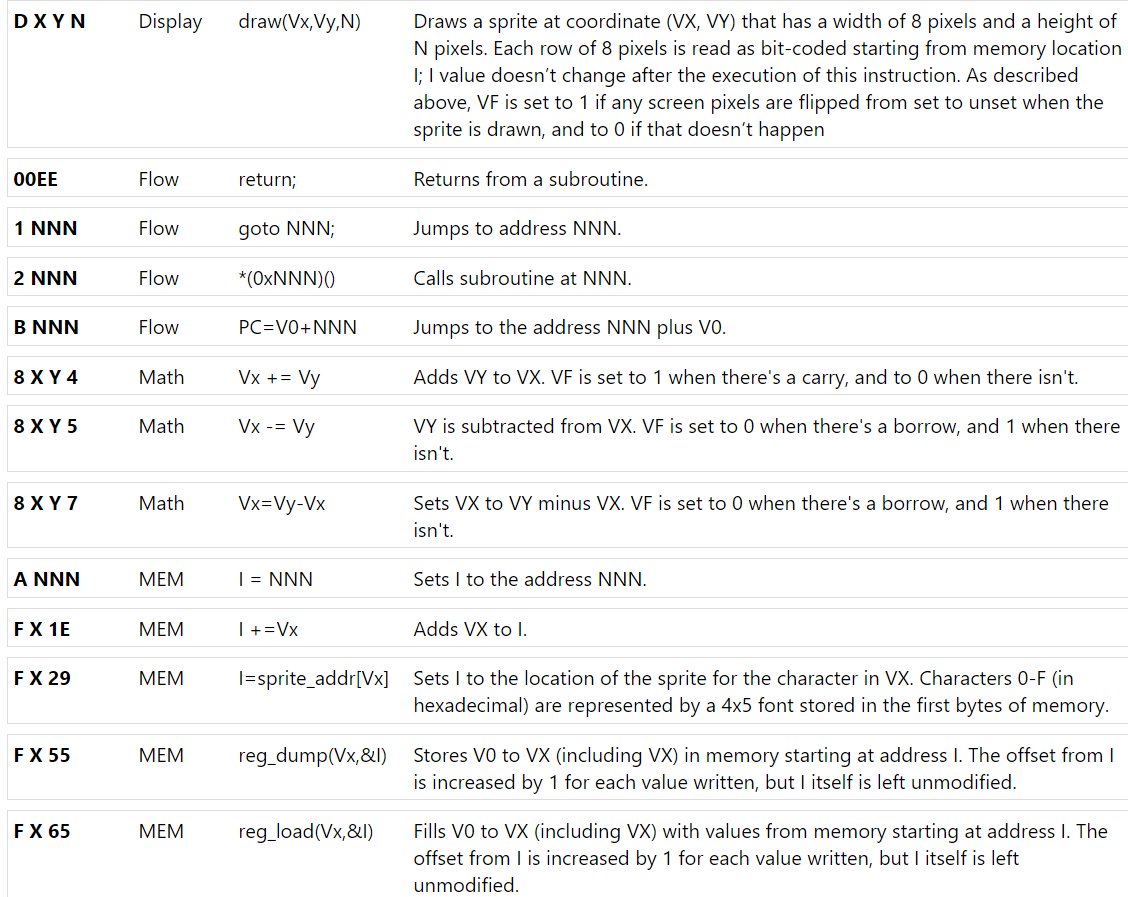
Obviously, to read from the protected memory, we had to execute some code to be able to access that memory. However, if we tried to set I to some memory within the protected range, we got the following error: SECURITY VIOLATION DETECTED: Can not set I outside of legal memory range.
Interesting, so that meant we had to find an alternate way to get I inside that memory range.
After a bit of reading, one instruction looked interesting: F X 29: Sets I to the location of the sprite for the character in VX
I immediately realized that for different values stored in VX, I would get set to a different location, so I could potentially get set to a location inside the protected memory.
Trying the following input:

The value of I was set to zero! We managed to access the protected memory!
Now, all I had to do was change the value inside VX (in my case V1), until I got access to the required memory.
I also realised, after a bit of trial and error, that I could read information from this memory using the display command D X Y N, with X and Y being co-ordinates, and N the height of the displayed output.
Displaying at V1=1:

However cool this output looked, it clearly wasnt the flag.
But, at V1=10, we hit a different output:

These are an interesting set of pixels.
Wait - what if the white pixels on the display were ones and the black zeros - thus leading to a binary output! Trying that on the first line, we get 01001000, which is the decimal equivalent of H! It’s the beginning of the flag!
Continuing with this method, we get the following binary output -
01001000 01100001 01100011 01101011 01010100 01001101 01111011 01100001 00110101 00110101 01100101 01101101 00111000 01101100 01100101 01100100 01011111 01110011 00110000 01100011 01101011 01110011 01111101
Converting this to ASCII, here’s our flag! HackTM{a55em8led_s0cks}
CHIP 8 /2
The challenge was as follows:
I made this sweet web-based chip8 emulator.
The last 512 bytes of memory are protected!
http://167.172.165.153:60003/
Note: This challenge can bee solved using only chip8 instructions.
We were given a chip8 emulator with a basic interface as follows:

And the following list of commands:


This challenge involves reading from the last few bytes of memory, which are again protected.
Messing around with the commands, it was pretty evident that there was no way to set I to anywhere in the last few memory addresses.
So what was the next possible thing? Code execution within that memory range. The command 2 NNN, which calls a subroutine at address ‘NNN’, was the command to accomplish this.
Using the command 2 E00, which calls the function at address E00 (4096 - 511 bytes, the first address in our forbidden memory), we get a weird error:

Invalid instruction: 5F61
It’s pretty clear that ‘5F’ and ‘61’ refer to the ASCII characters ‘_’ and ‘a’ respectively, but what does this mean? Could we be executing the hex values of the characters in the flag?
Let’s take another look. Executing step-by-step this time:
After a few steps we see something interesting:

Last instruction 'AA48'
Well, what do we have here? ‘48’ is the hex value of ‘H’, which is obviously the start of our flag!
From here on, all we have to do is gather the hex bytes from subsequent instructions, and skip forward an instruction when we hit an invalid instruction (continue execution from the next instruction).
Thus, we get the following collection of hex bytes:
48 61 63 6b 54 4d 7b 6a 75 64 36 65 5f 6a 75 72 79 5f 61 6e 64 5f 33 78 33 63 75 74 31 6f 6e 7d
And there’s our flag! HackTM{jud6e_jury_and_3x3cut1on}